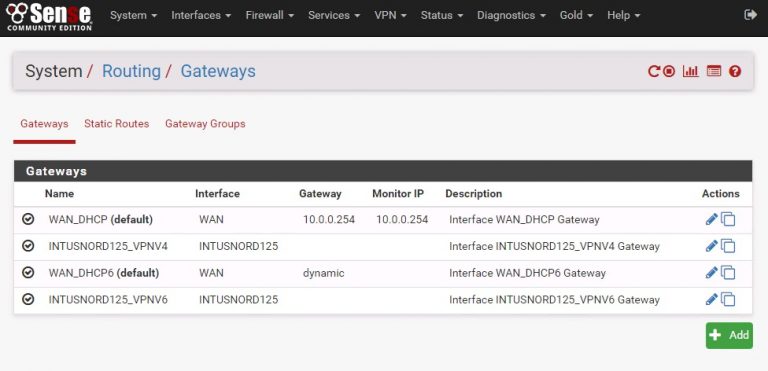
Now that the aliases are set up, we can configure routing. Select System -> Routing.
This screen will show all VPN connections and their interfaces. Each individual interface to be used as a potential gateway has to have testing parameters so that the firewall knows whether that interface is up and can be used.
First, you need to figure out some addresses that can be used for ping checks; if the ping doesn’t come back or is slow, pfSense will route to a better connection. You need to set IP addresses that are close and have fast ping times. I suggest DNS servers such as:
- 8.8.8.8
- 8.8.4.4
- 1.1.1.1
- 1.0.0.1
Once you know what test IP’s to use, edit each VPN interface and set the following (leave all others to their defaults):
- Gateway name : gwusnord1204 , for example
- Gateway monitoring : enable
- Monitor IP : here you put one of the IP’s listed above, something that can be pinged from this interface to determine if it’s up and has a good connection. Note – each IP has to be unique, you can’t use 8.8.8.8 for all connections.
- Description : something like the gateway name
- Poll interval : 1000
- Alert interval : 2000
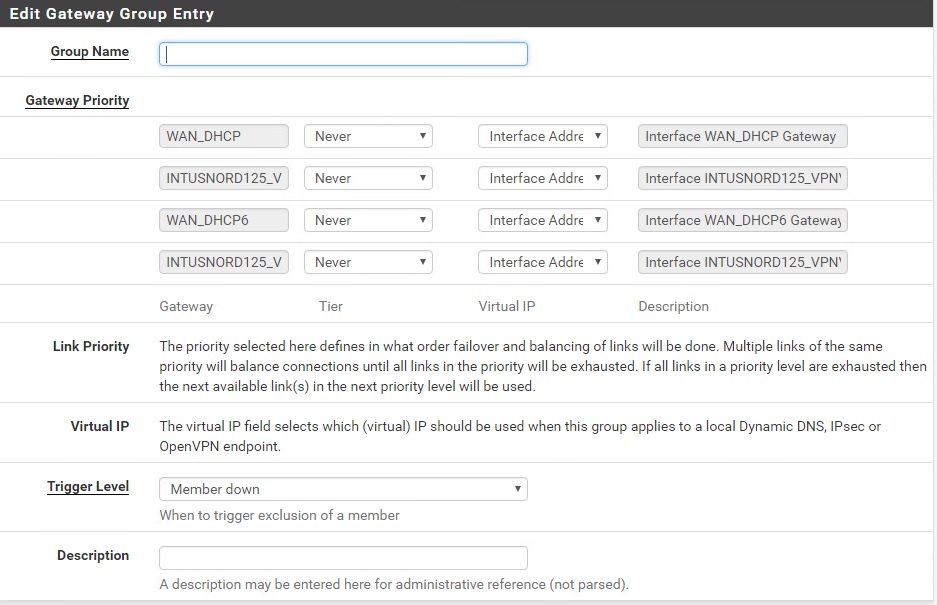
Once each interface is shaped, you can create the Gateway Groups. Go to System -> Routing -> Gateway Groups and add a new group.
The premise of the VPNSerialGroup is to try one VPN interface, then the next, then the next… With spread spectrum VPN your source IP address changes constantly, messing with secure sites. This route is used when you go to web banking or other secure sites, making your HTTPS connection not drop during use.
You want to rank the VPN connections in order of preference or just go top-down. Click on each INTUSNORDxxx interface and change “Never” to Tier 1, change the next to Tier 2 and so on.
Leave WAN* and other interfaces alone and set to the default “Never” – these routing groups are only for VPN interfaces.
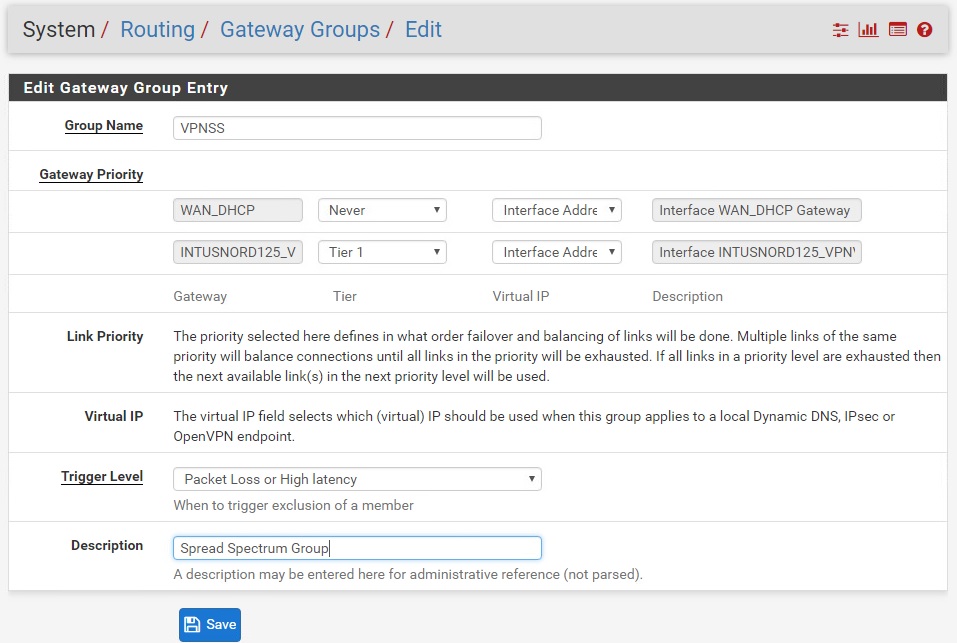
Set “Trigger Level” to “Packet Loss or High Latency” – this will fall through to the next interface if something is wrong with the current one.
Save when finished.
After the VPNSerialGroup is added, do the same to add the VPNSS group. It’s setup is identical to the above but for a major difference – set all VPN interfaces to Tier 1.
This routing group is the heart of using pfSense for a Spread Spectrum VPN, this is what causes connections to randomly go over various interfaces.
(Please note I was lazy with the connections and screenshots, my screenshot at right only shows a single connection – you should have four or more from the previous steps.)
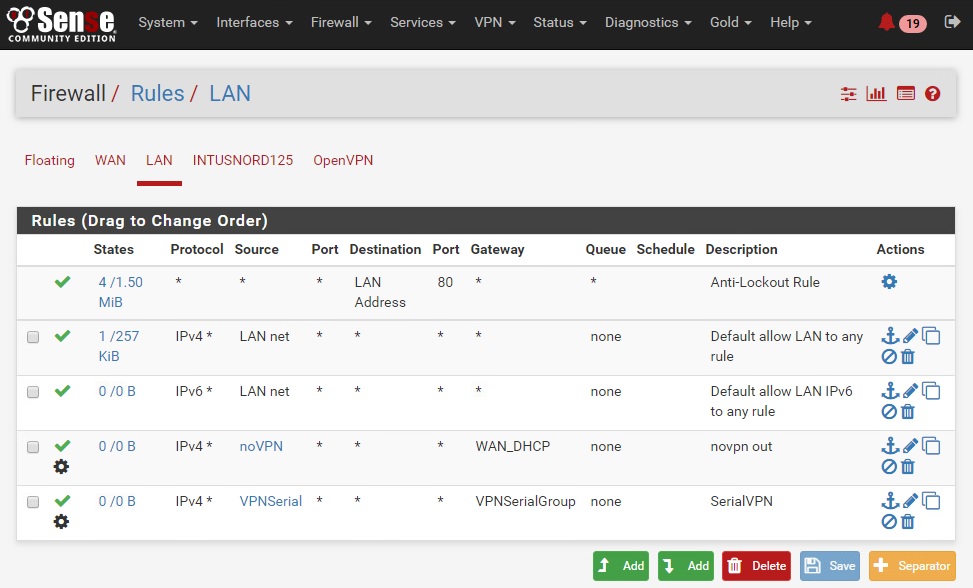
Time to add rules. Usually firewall rules are used to allow/deny traffic to and from locations, but in this case we’re putting in rules to tell the firewall that it’s not only okay to route to a different interface but under what conditions to do so.
NoVPN
First is the exception – from IP’s in this group, route straight out to the default gateway, no VPN.
From the Rules/LAN dialogue above, select Add with the down arrow to add a new rule at bottom. It’s parameters are as follows:
- Action: Pass
- Interface : LAN
- Address family : IPv4
- Protocol : Any
- Source : Single Host or Alias : NoVPN
- Description : NoVPN Direct
Select the Advanced Options / Display Advanced. From there:
- Gateway: WAN (hard set this to the default WAN interface, though “Default” does work in most cases)
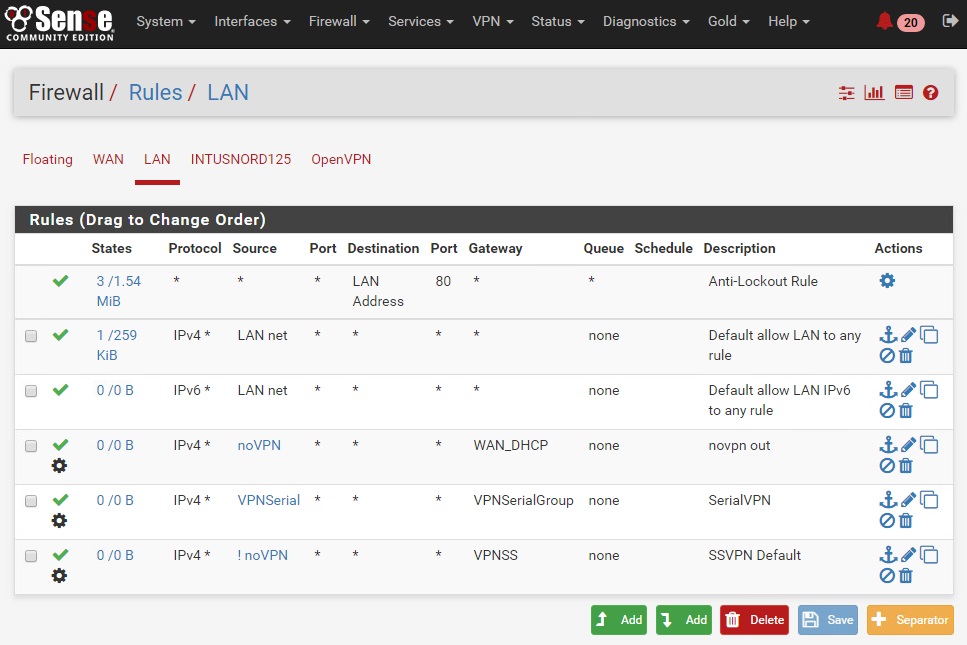
Serial VPN
Next, the hosts that should use the VPN, but only one channel at a time. This is helpful for obstinate websites, banking sites, etc.
From the Rules/LAN dialogue above, select Add with the down arrow to add a new rule at bottom. It’s parameters are as follows:
- Action: Pass
- Interface : LAN
- Address family : IPv4
- Protocol : Any
- Source : Single Host or Alias : VPNSerial
- Description : SerialVPN
Select the Advanced Options / Display Advanced. From there:
- Gateway: VPNSerialGroup
SSVPN
Lastly, the default group. If not NoVPN and not VPNSerial (handled above, then all else goes through the Spread Spectrum route.
From the Rules/LAN dialogue above, select Add with the down arrow to add a new rule at bottom. It’s parameters are as follows:
- Action: Pass
- Interface : LAN
- Address family : IPv4
- Protocol : Any
- Source : INVERT MATCH : Single Host or Alias : NoVPN
- Description : SSVPN Default
Select the Advanced Options / Display Advanced. From there:
- Gateway: VPNSS
These are the last steps – time to test what we’ve put together.