(Image from relevant story :https://yournewswire.com/man-sues-smart-tv-company-over-illegal-spying/ )
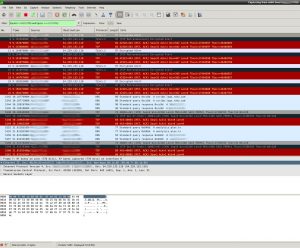
I decided to sit down for a couple hours and do a network packet capture to see how the Roku is ratting out what I’m doing exactly, and whether Plex is any less guilty – turns out there is a spiderweb of activity going on, these businesses are buttering each other’s toast and selling out us “consumers” any way they can.
We knew this, but it’s something else to see it flow across the wire. What follows isn’t everything – just highlights.
Roku has a number of business partnerships with Neflix, Facebook and others, sending encrypted data to each company at boot, a kind of handshake. Also at boot time it checks in with captive.roku.com which provides your Roku with a unique serial ID, then starts a steady stream of encrypted communication. The device then hits myipaddress.com to determine your public IP address which instantly tells them your Internet service provider and city and allows them to correlate all activity to your residence.
Once it provides you with a menu, every button press and selection is sent to *.logs.roku.com, the * being any number of semi-random hosts such as liberty|scribe|digdug|austin|giga|griffon|cooper.
I don’t know if it’s just because I have the Netflix app installed on the Roku, but it’s constantly talking to Netflix servers whether you’re using the app or not. A continuous stream of encrypted information is constantly being sent to servers such as occ-0-590-586.1.nflxso.net (Netflix Streaming services) even when just sitting at the main menu. The User Agent string clearly identifies your Roku device. On top of this constant flow of information are “logblobs”, large, gZip compressed and encrypted json objects sent via HTTP post. Note – I’ve never opened the Netflix app during this test, which was focused on Plex. It could be that Roku has a partnership with Netflix and they’re exchanging your data for privileged access to Netflix programming. With Net Neutrality dead, Roku has to butter their toast somehow or risk getting locked out.
Also, Roku has their own Certificate Authority, they don’t bother with standard services such as Thawte, Verisign, etc. This is more secure and surely saves them a good amount of money.
When you block captive.roku.com from resolving via your home DNS server, it falls back to its own internal – baked in – DNS server configs and tries to resolve it itself, bypassing your home network settings.
Once you start Plex as an app on the Roku, thus begins a steady encrypted stream to analytics.plex.tv, giving them all the information above plus a unique device ID which can then be correlated to your IP address which uniquely identifies your device and habits. captive.roku.com also learns of your use of the Plex app. While you’re browsing media in Plex, there’s a steady stream of data to analytics.plex.tv; it’s encrypted so I couldn’t see what was in it (filename? Movie / TV Show name? Can’t tell.)
What’s also unusual is a short data exchange every once in a while to TCP port 2350, a port not described in the Plex firewall configuration settings page (https://support.plex.tv/articles/201543147-what-network-ports-do-i-need-to-allow-through-my-firewall/). I frankly didn’t know what to make of this data.
Wikipedia confirms that Plex is soaking up a great deal of information:
On September 20, 2017, Plex announced a new privacy policy in which it was no longer possible for users of Plex to prevent their user data from being collected. However, in a later privacy policy update, Plex CEO Keith Valory stated that they will generalize the playback data and offer users the ability to opt out of sending more specific playback information.
It’s not trivial, but it is possible to trap these rats and watch your movies in peace.
When blocking traffic to and from the Roku and Plex, you have to allow things like api.roku.com or it won’t be usable. You can’t just wildcard block *.roku.com and *.plex.tv – you have to cut out specific hosts in specific ways.
To prevent your Roku hardware and Plex software from spying on you, you can do the following. Please note that if you are using some other SmartTV or player these steps won’t be as effective, but I do have generic steps at bottom that will still help.
Using Pi-Hole, block the following via Wildcard Blacklist:
- analytics.plex.tv (Key detail – this must be available when Plex starts! Disable afterwards.)
- captive.roku.com
- logs.roku.com
.. and block the following via Exact Blocking in the blacklist:
- plex.tv
In your firewall (I prefer PFSense), you should have an “egress rule” that prevents ports from “leaking” out of your network. For example, you won’t want TCP 135-139 or 445 leaving your network because you should never mount a window share over the public Internet. To your egress rules, add TCP/UDP 2350.
Here are some bonus things you can do which not only help with this situation, but hinder leakage from other Internet of Things devices in your house:
- Add to the Pi-Hole Wildcard Blacklist “myipaddress.com” – this will prevent appliances from fetching your public IP address and thus your internet service provider. Note – this means you won’t be able to use it yourself (there are many other sites you could use instead), and since there are other sites, not all IoT appliances will use this same one.
- If you have a SmartTV or other device, you can still use Pi-Hole to watch what addresses it tries to resolve and if you come across something like “analytics.panasonic.com” (if you have a Panasonic TV, for example), you can block that and if your TV still works as expected, you win.
- Use of Pi-Hole prevents advertisements from getting to your Roku and other devices as well, which are otherwise streamed with merciless impunity.
- Add a new rule to your LAN -> WAN rule blocking the DNS providers that you know you don’t use, which prevents IoT appliances from bypassing your DNS rules (and your Pi-Hole installation). I for example use 1.1.1.1, so I can block 8.8.8.8 and 8.8.4.4 (Google’s DNS servers), commonly used in IoT appliances. Roku uses bersl2.info, which I blocked too.