This site has a few features that set it apart from most. These security measures aren’t because the site has super secret cow powers or secret content (everything’s public, open source works), they reflect modern security standards that, in truth, everyone just needs to get used to.
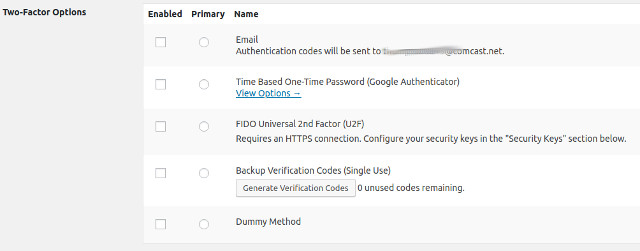
Multifactor
No doubt about it, multifactor can be a pain. If you remember your password and type it in, you still need to get a separate device out – probably your smartphone – to get the multifactor code. This can be annoying but it’s a necessary evil because passwords are very often weak or stolen. You need to enable multifactor everywhere you can (GMail, Evernote, Facebook, etc). Embrace multifactor – it’s here to help.
Login via username, not email address
In many cases, email addresses are an extension of our identity. It’s on our business cards, lease agreements, accounts for monthly payments (etcetera), and as a result changing your primary email address can be a REAL pain. This being the case, your ex knows it, your parents know it, your employer knows it…. anyone who bothers to pay attention knows your email address.
On the other hand, usernames can vary from site to site. You not only have to guess a user’s password but guess what name they used. This also helps with anonymity.
Long passwords
NIST has admitted that it made a mistake a long time ago – passwords don’t need to be C0mp.l.3x!! , they need to be long. Length is more important than content, the longer it is the stronger it is.
For this and every site you use everywhere, make your password as long as is convenient and as simple as the site will allow. Always use multifactor and install good antivirus software on your computers (not McAfee or Symantec, for Pete’s sake..). That is practical security.
Must be registered and logged in before posting
Many sites are doing this nowadays, which is inconvenient. The reason is that spammers and criminals use open board postings to post sites to exchange illegal material, or otherwise small, innocuous post will end up with literally thousands of advertisements for “!!!V1Agr@!!! BUY IT RIGHT NOW NOW NOW!!!!” … it’s disgusting. There’s only so much a site can do to protect itself, so unfortunately this passes inconvenience to you, the user.
Few spammers go through the trouble to set up multifactor before they spam a website, and those that do are easily caught, removed and blacklisted.
Minimal logging & cookies
This site is fronted by Cloudflare, they may use cookies for general analytics so that they can determine who’s hitting the site from what country using what browser… and that’s it. We chose Cloudflare because they’re privacy-minded and not invasive, but their specifics are out of our control and are subject to change. Cookies on this site enable basic site function – we use no tracking cookies of any kind.
The central server keeps diagnostic logs on a ramdisk, rotated out every week. After that week we only keep what we need – no IP’s are held onto, no visitors are tracked beyond what Cloudflare uses for basic visitor count. We know the last time you logged in (but not from what IP address) and what you’ve posted. Law enforcement requests for data that are legal and accompanied by a warrant we are obligated to abide by, but it won’t be much.
In the end, we know our site was (for example) hit 1000 times this week with Firefox (560 times), Chrome (400) and IE (40) from the US, Canada and Russia… and even that data is gone in 6 weeks.