Your Internet access is being surveilled. Says so right in your agreement, which you “agree to if you continue to use [this]service”:
https://www.xfinity.com/Corporate/Customers/Policies/SubscriberAgreement?rid=10010075335&mid=20210508_Adhoc_CM_Crisis_UpdatedResiSvcAgreement
MONITORING AND RECORDING
You agree that we (and our agents) may monitor and record any telephone calls or other voice communications, data, or images transmitted between: (1) us and our agents, and (2) you, your agents, any user of your Services, your Customer Equipment, or any user of any phone numbers associated with your account.
If you don’t like it, then don’t use their service, right? Problem is of course it’s in every service agreement you could possibly find, there is no provider what won’t say the same thing since everyone gets their lines from CenturyLink (including Comcast), and CenturyLink used to be Level(3), and do you know who Level(3)’s biggest customer was? The US Government.
The aim of this project is to use pfSense or OpenSense (open source firewall solutions) to both encrypt information in and out of your house and split it up across multiple connections. This makes metadata regarding your internet activity practically useless. It’s what the government does to prevent other governments doing to them what they do to us, and you can do it too for free.
(Infographic by Vikram Jaiswal, slideshare.net)
Spread Spectrum was originally invented by Hedy Lamarr in the 40’s to prevent jamming during the war.
It has since been embraced both by modern wireless phones we use in our houses (DECT) and by corporations looking to improve their own security via products only available to big business, well out of reach of the public.

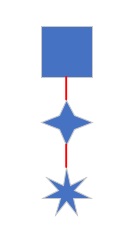
When you sign up with a VPN provider (such as NordVPN) and install their client software, the diagram at left shows what the connection looks like:
- your home network (the square)
- connects to the VPN provider’s servers (4-point star),
- which then connects to the website on your behalf.
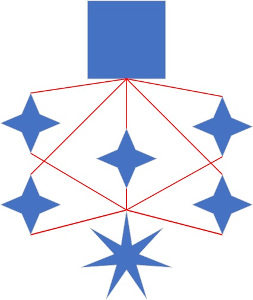
The diagram at right (and thus the logo for the project) at right depicts five connections from your house converging on a given website. In this case, your home firewall (such as pfSense) is connected to all five VPN providers at once. pfSense will fracture the traffic across all five connections.
- this scrambles metadata from each connection
- this system applies to the whole house, protecting every device and endpoint without the installation of VPN software (and ensuring it’s always turned on!)
- Because it’s at the household level and across multiple simultaneous connections, it’s now impossible to analyze metadata. Is this your phone looking for updates, your Windows 10 machine looking for updates or you visiting cnn.com?
- You can split up traffic across multiple providers too – go ahead and get Comcast, Centurylink DSL and Verizon 4g, get the cheapest lines they offer and then multiplex them into a single, fault tolerant line that’s faster than the overall additive bandwidth (due to compression)!
Is this level of security over the top, is it worth the work? Ask yourself two questions :
- Why do businesses and governments do this?
- Why can’t I? Why do absolutely no residential grade devices or applications allow me to do the same thing they’ve been doing for decades?
Can you monitor big businesses? Oh hell no, not when they’re using this technology. Can they monitor you? Absolutely and they have been (I didn’t make up the metadata fingerprinting above on my own, that’s how it works). The death of Net Neutrality has made our situation much, much worse.
With this system in place you can enjoy the same level of security and privacy with greater resilience (how often does your ISP’s service drop?) and you spend less money (buy the cheapest circuits they offer and aggregate them together).



