Here’s what you need to make this project happen for you. This article series is written assuming it will be implemented at a house or other residence but it can be used for cheap-and-very-effective business-to-business networking too, allowing your small business to have the same level of security as your bigger competition.
A desire to tink around
Even after this is all installed, this solution requires a little care and keeping. Sometimes you change VPN providers or their datacenters will go down. More and more often sites are blocking VPN addresses because they know they can’t throw advertisements at you and track your activity so, with the death of Net Neutrality, they just block you outright. This can be a real pain in the tail when your children want to watch Netflix or your husband wants to quickly check his bank account balance before going to work, only to find that both services are temporarily unavailable without messing with the firewall.
This system can be disruptive to average home use but it’s important to understand why: five years ago this system would have always worked under every context, but now providers block you from their content knowing that they can’t track you over a VPN. Every context where this system gets in the way of average home use has a single cause, which are businesses choosing to block you because they can’t track you.
Therefore, consider the fact that, after you install this and something doesn’t work, that was another way you were being tracked and didn’t know it.
Lastly, don’t worry too much about not being able to ever watch Netflix again or anything – there are a couple convenient ways to temporarily not go over the VPN and go straight out to the Internet as needed. More on that later.
Lastly, it’s really easy to go to nordvpn.com, give ’em a credit card number, download their software and be done with it. Do this with every machine in your house and you’ll do way better than you are now. This is not that easy solution.
Terminology level-set
We need to be on the same page regarding terminology first. Let’s start with “bridges bridge and routers route”:
- Bridge – a bridge is a network device that converts from one media type to another. Comcast comes in via coaxial cable that plugs into your TV, and a bridge turns that into an ethernet connection that you can plug your computer into.
- Router – a network device that routes packets from one place to another. A router will figure out if you’re trying to get somewhere on your local network (the printer) or on the Internet (google.com).
- Firewall – Something that allows traffic out but restricts traffic back in. Your workstation is allowed to go to www.google.com, but Google is not allowed to scan your computer or home network – this happens because of your firewall, either a network device or software you can run on your computer, or both.
- “modem” – a piece of hardware used in the 70’s, 80’s and 90’s that MODulates a computer signal so that it can be sent over a phone line, and the person/computer on the other end DE-eMulates that signal back to something a computer can use. The word “modem” has become like “Wi-Fi” – WIreless does not have FIdelity and modems are no longer used: they’re marketing terms / buzzwords. When people talk about modems now they are referring to devices sold by Comcast, Cox or CenturyLink to provide Internet service, but they’re not actually modems. When I use the term “modem” in this article it’s because it’s commonly referenced so most people will know what I’m referring to.
- IP address – all computers have an address not unlike a postal address, and it usually looks like 192.168.1.53. For example, if your home computer is 192.168.1.53 and your firewall/router is 192.168.1.1, your PC at .53 will route through .1 to get to www.google.com at 8.8.8.8.
- subnet – we have home networks, they’re usually “flat” which means everything can find everything; your laptop can “see” the TV and your smartphone can “see” your TV too – they’re all on the same network. A subnet is a slice of a network, a separate piece that can be used to isolate network participants. In this project we’ll change your home network from a /24 to a /28 such that the firewall will know how to handle certain machines, yet all network members will still be able to see each other.
- ISP – Internet Service Provider, such as Cox Cable, Comcast, CenturyLink DSL, Verizon 4G hotspot, etc. Business class, XFinity…. whatever.
Home Firewall
Modern home Internet devices are all-in-one routers, bridges and firewalls. When Comcast, Cox or CenturyLink provides Internet service, they give you a device (or you can go to Best Buy and get one of your own) that they plug their line into and you plug your computer into and there you go: Internet access.
The problem is that you don’t own that device, Comcast/Cox/CentiryLink does so it does their bidding, not yours. There are very many documented cases of Comcast scanning people’s home networks to see what’s inside the house, and now that Net Neutrality is gone they can flag your house to send you specific advertisements at the router level (Verizon and AT&T already did this with your smartphone: your web traffic is flagged to differentiate your activity to ad providers).
Put another way, this combination device controls how your home is protected and the way your Internet activity flows, and it’s not working on your behalf.
Even if the Internet Service Provider is completely innocent, their stock “modems” get compromised / back doored / hacked all the time, and now a hostile third party controls your home internet access at a fundamental level.
What you need is your own firewall.
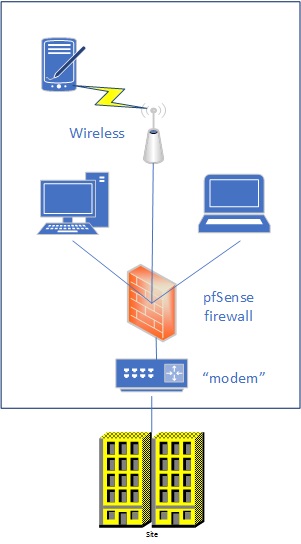
The diagram at left shows an average home network with a single component that most are missing : a firewall.
Usually people plug their computers, wireless devices, TV, DVD player et al directly into the “modem”, trusting their service provider to protect these home devices.
This project requires the installation of the orange device at left. The firewall plugs into the “modem”, your wireless device plugs into the firewall and then all your other home computing devices plug into the back of the wireless device.
To actually build the home firewall is outside the scope of this article, but you essentially get an old laptop or desktop computer (very little power is needed), connect another network device (such as a network card or USB network adapter) and install pfSense or OpenSense.
A VPN provider
There are a number of solid VPN providers out there, you need to pick one that’s best for your pocketbook and use case. The ones listed below I list in order of my own preference.
- NordVPN (nordvpn.com) – an excellent provider with good customer service and a decent cost point.
- ExpressVPN
- Tunnelbear
- Mullvad
Selection criteria include:
- Cost: don’t go cheap, but it’s not necessary to get the most expensive thing out there either.
- It’s best for pfSense/OpenSense to connect to VPN providers using OpenVPN, so you need someone who’s compatible. If they say they’re Linux and Mac compatible, they probably can use OpenVPN.
- The more servers the better. If they advertise “100+ servers!” then they’re s small fry shop, but if they have tens of thousands all over the world then a) you can start shopping amazon.co.uk if you want to, and b) have access to any number of VPN servers here in the ‘states.