Note – Comcast cable or CenturyLink “modems” aren’t really “modems” – they don’t MOdulate or DE-EMulate anything. A carry over from the old phone system modem days, this is a buzzword like “Wi-Fi” (Wireless doesn’t have Fidelity, it has signal strength). These devices are technically bridges – bridging one medium such as cable to another which is ethernet. These devices are referred to as bridges, below.
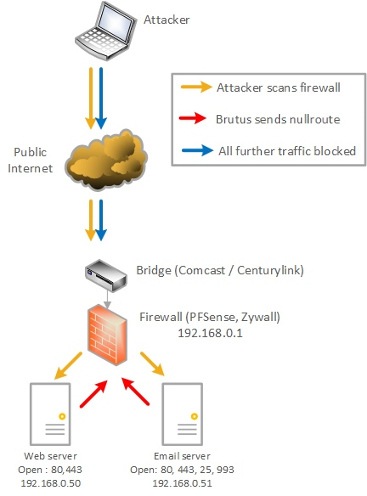
An Intrusion Prevention System is something that actively blocks attacks (as opposed to an Intrusion Detection System, which simply calls your attention to and logs attacks). Brutus is a series of scripts used in conjunction with the Ubuntu Portsentry package that blocks the reconnaissance phase of an attack – the attacker (be it human or program) first has to scan your network to see what’s open and then base an attack on the information gained. Portsentry detects this “poking around” and executes Brutus to instantly drop the source for a number of days, making reconnaissance against your network very frustrating.
In this diagram the attacker is depicted as someone at a laptop, but in most instances nowadays it’s just another program looking for vulnerable networks to automatically attack.
Whether you’re a business or at home, people and programs “rattle your doorknob” to find a way into your network all day, every day. Even if you don’t have a DMZ and your own web or email server, Comcast has been caught scanning people’s internal networks and the Internet of Things sometimes makes your home network devices prime targets. It’s best to run your Comcast cable or Centurylink DSL “modem” in bridge mode and have a firewall behind it (such as PFSense), which prevents this activity.
In a home environment, Brutus would block everything that touches your network. In a business / small business where you’re running a server, Brutus would block scans but NOT block valid requests.
Consider the following scenarios:
- A valid user wants to get to your website. They hit www.mysite.com (for example) and it routes to your web server, port 80 or 443. No problem – that port is managed by Apache or NginX and the website comes up.
- Someone sends an email to a server you host – inbound emails arrive on TCP 25 which is handled by Postfix – the email is handled and everything works fine.
- An attacker wants to find out what ports are also open. Have you made a mistake of running telnet, or do you use FTP to manage your website? FTP shouldn’t be open on your mail server, nor do you have telnet open on your web server. All these “touches” are detected by Portsentry, which instructs Brutus to null-route the source IP for a day or three – attack stopped.
- You’re not a business but a home user. Are you running a “modem” with port 37215 open and you didn’t know about it? Is the Comcast management port open? What are they vulnerable to? When attacker or botnet scans your home network Portsentry detects that scan and drops the source instantly. After you install Brutus you’ll find you’re null-routing IP’s on the Internet you never visited, but they’ve been “rattling your doorknob” for howeverlong and you never knew it.
This system as an IPS is not radical, businesses have had systems that do this for quite some time – what’s different about this is that it works for businesses as well as at home and it’s free as in beer.
The components of the Portsentry & Brutus system are: